1 – Criar VMSERV 1 – Criar AUTORIDADE Certificadora
/certificate add name=CA-VPN-ex country="Br" state="AP" locality="Beira Rio" organization="VMSERV 1" unit="Ti" common-name="CA-VPN" key-size=4096 days-valid=3650 key-usage=crl-sign,key-cert-sign2 – Assinar a AUTORIDADE Certificadora
/certificate sign CA-VPN-ex ca-crl-host=127.0.0.1 name="CA-VPN"3 – Criar certificado SERVIDOR
/certificate add name=SERVIDOR-ex country="Br" state="AP" locality="Beira Rio" organization="VMSERV 1" unit="Ti" common-name="SRV-MK-OPVPN" key-size=4096 days-valid=1095 key-usage=digital-signature,key-encipherment,tls-server4 – Assinar certificado SERVIDOR
/certificate sign SERVIDOR-ex ca="CA-VPN" name="SERVIDOR"5 – Criar certificado CLIENTE
/certificate add name=CLIENTE-ex country="Br" state="AC" locality="Beira Rio" organization="VMSERV 1" unit="Ti" common-name="CLIENTE" key-size=4096 days-valid=3650 key-usage=tls-client6 – Assinar certificado cliente
/certificate sign CLIENTE-ex ca="CA-VPN" name="CLIENTE1"7 – Exportar CA e Cliente
/certificate export-certificate CA-VPN export-passphrase=""
/certificate export-certificate CLIENTE1 export-passphrase=1234567898 – Criar o IP Pool OPVPN
10.0.80.10-10.0.80.20
9 – Criar o Profile OPVPN
IP Local: 10.0.80.1 IP Remoto: OPVPN Pool
10 – Criar a Secret
Usuário: vmserv
Senha: Vms#0156
IP: 10.0.80.11 (Um IP por usuário, em sequência)
11 – Configurar o OPVN SERVER indicando o OVPN Profile.
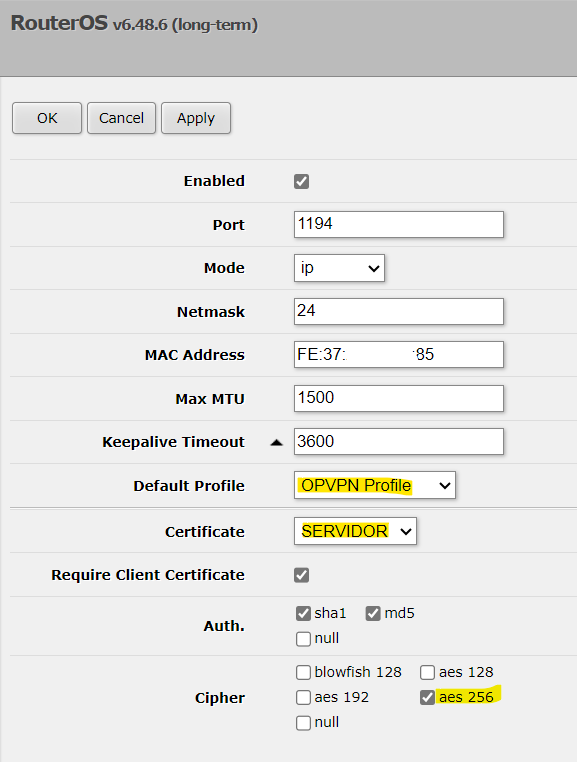
12 – Baixar os arquivos de certificado em Files, abrir certificados pelo Bloco de notas e preencher o arquivo de configuração.
client
dev tun
proto tcp-client
remote XXXXX.sn.mynetname.net
port 1194
nobind
persist-key
persist-tun
tls-client
remote-cert-tls server
<ca>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</ca>
<cert>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN ENCRYPTED PRIVATE KEY-----
-----END ENCRYPTED PRIVATE KEY-----
</key>
verb 4
mute 10
cipher AES-256-CBC
ncp-ciphers AES-256-CBC:AES-128-GCM:AES-128-CBC
auth SHA1
auth-user-pass vmserv-secret.txt
auth-nocache
;redirect-gateway def1
route 10.0.80.0 255.255.255.0
; Rota para a rede VPN
route 192.168.2.0 255.255.255.0
; Rota para a LAN13 – O arquivo vmserv-secret.txt deve conter USUÁRIO e SENHA (criado na secret, um por linha)
vmserv
Vms#0156Referências bibliográficas:
